A New Player in the Ransomware Game - Cybercriminals are constantly evolving their tactics, and the latest twist is something that should make every IT and cloud administrator sit up. A new Ransomware-as-a-Service (RaaS) platform called shinysp1d3r has surfaced, and unlike traditional ransomware that usually hits Windows endpoints, this one goes straight for the jugular—VMware ESXi hypervisors and their datastores.
The group behind this? The notorious ShinyHunters, an eCrime syndicate already infamous for high-profile data breaches and extortion campaigns. With shinysp1d3r, they appear to be taking their game to the next level, zeroing in on virtualized infrastructure that powers critical business operations.
Why VMware ESXi Is a Prime Target
VMware ESXi is the backbone of many enterprise data centers. By compromising the hypervisor itself, attackers don't just disrupt a single machine—they can cripple entire virtual environments at once.
Once shinysp1d3r makes its way in—usually through stolen SSO credentials or SSH keys—it spreads laterally across ESXi clusters. It disables snapshots, suspends running VMs, and then begins AES-256 encryption on every VMDK file simultaneously. That means businesses face massive downtime, data lockout, and, of course, the dreaded ransom note.
To make matters worse, affiliates of the ransomware can tailor the attack using a control panel. They can pick which datastores to encrypt, choose file extensions, and even throttle network usage to slip past monitoring tools.
Under the Hood: How Shinysp1d3r Works
The architecture is as professional as it is malicious. At its core, shinysp1d3r relies on:
The "Urgent Message" Note
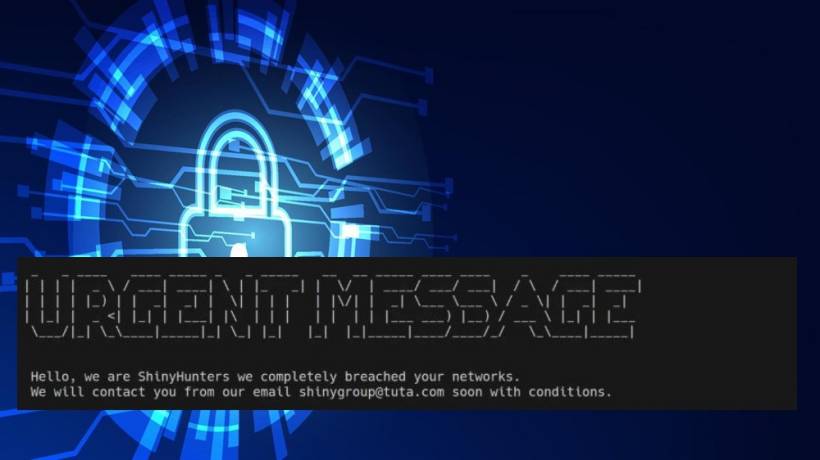
A chilling screenshot of the attackers' ransom note—rendered in blocky ASCII art—makes the threat painfully real: "Hello, we are ShinyHunters we completely breached your networks," it reads, and it even gives a contact email shinygroup@tuta[.]com for "conditions." Mentioning the email so plainly is part of the playbook: it signals the intruders are ready to negotiate or extort and is meant to rattle defenders into making rushed decisions. If you see a message like this, treat it as a confirmed indicator of compromise, preserve the artifact for forensic analysis, avoid direct engagement with the listed address, and escalate immediately to your incident response team so you can contain the incident and follow legal and regulatory notification steps.
The entry points are depressingly familiar: weakly protected SSH keys, misconfigured servers, or stolen SSO tokens obtained through social engineering and AI-powered vishing attacks. Once inside, the malware wipes logs and disables external syslog forwarding to cover its tracks.
Why This Is More Dangerous Than "Ordinary" Ransomware
Most ransomware campaigns hit desktops or file shares. Shinysp1d3r's focus on the virtualization layer means attackers can effectively hold an entire data center hostage. Businesses would either need to restore from completely isolated backups or consider paying up.
This evolution shows how ransomware groups are professionalizing. They aren't just encrypting files anymore—they're building full-fledged cloud-centric extortion platforms with dashboards, chat widgets, and affiliate programs.
What Organizations Can Do Now
While shinysp1d3r is still under development, early detections are a clear warning. Companies should be acting now rather than waiting for the first wave of mass attacks. Some key steps include:
get-carrot-zoom[.]com and recurly-zoom[.]comFinal Thoughts
Shinysp1d3r signals a worrying trend in the ransomware landscape: the shift from endpoint-focused attacks to virtualization and cloud-layer attacks. As businesses continue to migrate workloads to virtualized and hybrid environments, attackers are following suit.
The lesson here is simple: if your organization relies on VMware ESXi or similar hypervisor environments, treat this as a wake-up call. Strengthening defenses today may be the only way to avoid becoming tomorrow's headline.





Comments