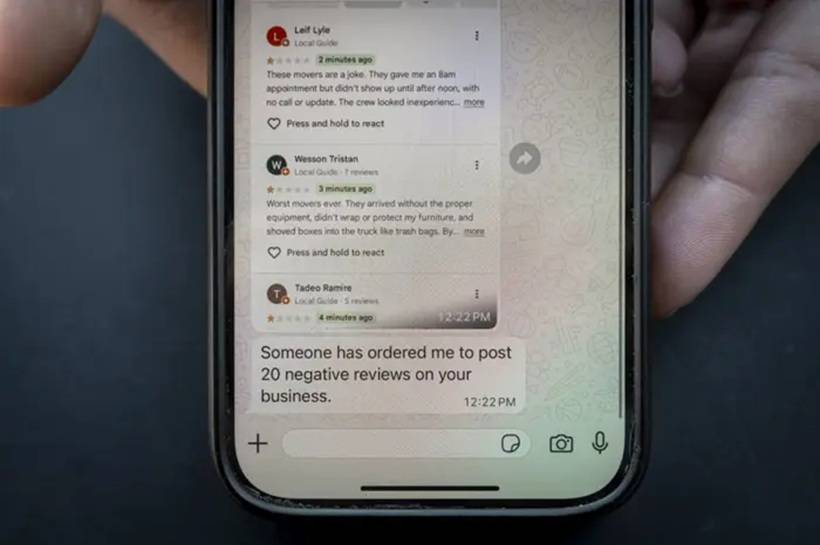
A Message That Changed Everything - In June, Los Angeles contractor Natalia Piper was busy juggling her day-to-day business when a strange WhatsApp message appeared. The sender, using a number from Pakistan, bluntly stated: "Someone has ordered me to post a negative review on your business. Got an order to post 20 reviews."
LEMON BLOG
When you think of Windows BitLocker, you probably imagine a strong, locked vault that keeps your sensitive data safe from prying eyes. But like any complex piece of software, even the strongest vault can develop cracks. In September 2025, Microsoft disclosed two newly discovered vulnerabilities in BitLocker that could let attackers slip through the cracks and gain the highest level of control on a Windows system
When Trust Is Hacked - In early 2024, a multinational company lost over US$25 million in a shocking scam powered by deepfake technology. Attackers used artificial intelligence (AI) to impersonate a senior executive during a video call, tricking finance staff into transferring funds.
Cloud security often makes headlines for sophisticated breaches, but sometimes the biggest risks come from the simplest mistakes. One such case emerged when a publicly accessible JSON configuration file (appsettings.json) leaked Azure Active Directory (AD) credentials, giving attackers the potential to waltz straight into Microsoft's cloud ecosystem.
Google has once again found itself in the spotlight of cybersecurity discussions, but this time for a worrying reason. A newly discovered vulnerability in Chrome's ANGLE graphics library has raised red flags among security experts worldwide. Labeled CVE-2025-9478, this flaw is no small glitch—it carries a CVSS 3.1 score of 8.8, putting it firmly in the "high severity" category
LEMON VIDEO CHANNELS
Step into a world where web design & development, gaming & retro gaming, and guitar covers & shredding collide! Whether you're looking for expert web development insights, nostalgic arcade action, or electrifying guitar solos, this is the place for you. Now also featuring content on TikTok, we’re bringing creativity, music, and tech straight to your screen. Subscribe and join the ride—because the future is bold, fun, and full of possibilities!