For many of us, browser extensions are simply helpful add-ons. We install them to make browsing easier, to boost productivity, or to get features the browser doesn't provide by default. But every now and then, a case emerges that reminds us of an uncomfortable truth: not everything inside the Chrome Web Store is as safe as it looks.
Recently, cybersecurity researchers uncovered two seemingly "legit" Chrome extensions that turned out to be anything but harmless. Both carried the same name — Phantom Shuttle — and both were quietly stealing user credentials while pretending to be useful networking tools.
When a "Helpful" Tool Becomes a Silent Spy
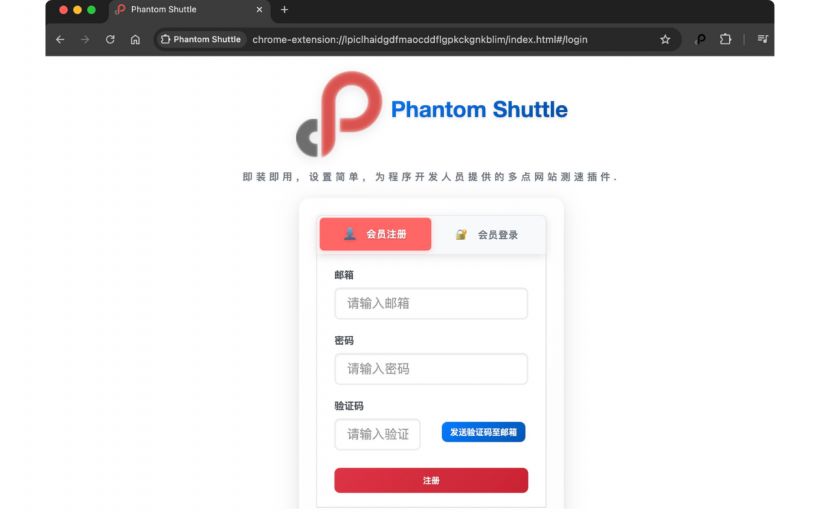
Phantom Shuttle was marketed as a multi-location network speed testing extension, supposedly meant for developers, international users, and businesses involved in overseas operations. On the surface, it looked convincing. It had a professional interface, features that appeared to work, and even a VIP subscription model where users paid to "unlock" better proxy functionality.
But once users activated this VIP mode, the extension revealed its real purpose. Instead of simply testing network speeds, it began intercepting browser traffic, injecting credentials automatically, and routing connections through servers controlled by the attackers. Everything happened silently in the background while users believed they were simply using a premium VPN-style tool.
How It Managed to Stay Hidden for So Long
One reason this operation is so alarming is because of how sophisticated and patient it was. Phantom Shuttle wasn't some overnight pop-up scam. One version had been around since 2017, while another appeared in 2023, both functioning in almost identical ways. The extensions were even designed to "look busy" and legitimate, running real latency tests and showing live connection data so users would feel confident they were using a genuine product.
Behind the scenes, malicious JavaScript inside the extension was automatically injecting hard-coded proxy credentials whenever websites required authentication. This allowed the attacker to quietly hijack traffic without prompting the user for any credentials. From there, the extension selectively routed traffic from over 170 major websites through attacker-controlled proxies.
This wasn't limited to random sites. It specifically targeted high-value platforms such as developer tools, cloud platforms, major tech services, corporate systems, social networks and even adult websites — the latter very likely included for potential blackmail leverage.
What Kind of Data Was Being Stolen?
Once Phantom Shuttle gained control, the attackers effectively sat in the middle of users' internet traffic. This position allowed them to capture almost anything sent through those connections. That includes usernames, passwords, cookies, session tokens, credit card data, browsing activities, form submissions and even developer API keys or corporate access credentials.
For individual users, this already poses a serious privacy and financial risk. But for developers and organisations, it opens the door to much larger consequences such as corporate data breaches, compromised systems and potential supply chain attacks. In other words, this wasn't just a nuisance — it had the capability to become a major cybersecurity incident.
A Well-Organised and Long-Running Operation
Nothing about this looked amateur.
Payment systems were properly integrated using platforms like Alipay and WeChat Pay. The infrastructure was hosted on Alibaba Cloud. The interface was polished and convincing. And to make matters worse, the extensions regularly "phoned home" to a command-and-control server, transmitting email addresses, plaintext passwords and other metadata at frequent intervals. The fact that this appears to have gone on for nearly eight years only proves how carefully this spyware was built and maintained.
While it's still unclear exactly who is behind Phantom Shuttle, the language used, payment integrations and infrastructure strongly suggest that this was a China-based operation.
Why This Should Concern Everyone
This incident is a powerful reminder that browser extensions are not harmless little toys. They sit inside the very application we use to access banking portals, cloud dashboards, social media accounts, developer environments and corporate systems. When abused, they become one of the most dangerous and overlooked attack points.
The Chrome Web Store creates a sense of trust. If something is listed there, many users assume it has already been vetted and is therefore safe. Phantom Shuttle proves that this isn't always the case.
If You Installed Phantom Shuttle — Act Now
Anyone who has used Phantom Shuttle should remove it immediately. Do not simply disable it. Uninstall it completely, then change passwords for important accounts, enable two-factor authentication where possible and monitor for unusual activity. If the extension was used on a work device, it is also important to alert the relevant IT or security team.
Final Thoughts
The Phantom Shuttle discovery shows how modern cybercriminals are no longer just throwing together obvious scams. They build polished, subscription-based "products," hide malicious features behind legitimate functionality and rely on user trust in official platforms to stay undetected.
Users believed they were paying for a helpful VPN-style tool. Instead, they were paying to expose their own data.
If there is one takeaway from this, it is simple: always be cautious when installing browser extensions, especially those that handle proxies, networking, or anything related to internet routing. Convenience should never come at the cost of security — because with extensions like this, the price can be far greater than what you paid for the subscription.






Comments