A major security vulnerability has been uncovered in the Veeam Updater component, a key part of various Veeam backup solutions. This flaw, identified as CVE-2025-23114, could allow hackers to execute malicious code on affected servers by launching a Man-in-the-Middle (MitM) attack. If successfully exploited, attackers could potentially gain root-level access, putting sensitive data and critical systems at risk.
What's the Issue?
This vulnerability has been assigned a CVSS rating of 9.0, making it an extremely high-risk security concern. The issue stems from the Veeam Updater's insecure communication channels, which fail to properly validate TLS certificates when transmitting sensitive data. As a result, attackers who position themselves between the vulnerable system and its update server can intercept and modify update requests, injecting malicious code into the system.
What Could Go Wrong?
If exploited, this flaw could give attackers full control over a targeted system, enabling them to:
- Veeam Backup for Salesforce (versions 3.1 and older)
- Veeam Backup for Nutanix AHV (versions 5.0 and 5.1)
- Veeam Backup for AWS (versions 6a and 7)
- Veeam Backup for Microsoft Azure (versions 5a and 6)
- Veeam Backup for Google Cloud (versions 4 and 5)
- Veeam Backup for Oracle Linux Virtualization Manager and Red Hat Virtualization (versions 3, 4.0, and 4.1)
Veeam has responded to this vulnerability by releasing updated versions of its affected software, addressing the security flaw within the Veeam Updater component. However, organizations using outdated versions remain vulnerable and should take immediate action.
How to Protect Your System
To mitigate the risk associated with this vulnerability, administrators should take the following steps:
<log_bundle>/veeam/veeam-updater/updater.log). ✔ Use the Veeam Updater Tool – Run the built-in tool to install the latest security updates. ✔ Enhance Security Measures – Implement network monitoring and isolate backup appliances from unnecessary external access.Fixed Versions
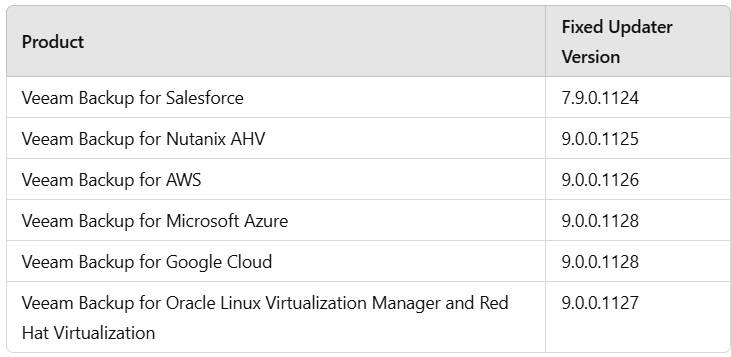
Veeam has patched the vulnerability in the following fixed Updater versions:
Final Thoughts
With a CVSS score of 9.0, CVE-2025-23114 is a critical security threat that should not be ignored. Organizations relying on Veeam backup solutions must act quickly to apply patches and implement additional security safeguards to prevent exploitation. Keeping your software updated and monitoring for suspicious network activity is key to ensuring your backup infrastructure remains secure.
Don't wait—update your Veeam Updater component today!